In Windows environment, each domain and local user, group and other security objects are assigned a unique identifier — Security Identifier or SID. It is an SID, but not the username, is used to control access to different resources: network shared folders, registry keys, file system objects, printers, etc. In this article we’ll show you some simple ways to find the SID of a user or group (Active Directory or local), and the reverse procedure – how to get the name of a Windows user or group by a known SID.To convert username to SID, you can use the excellent tool from the Sysinternals toolset – PsGetSid. But you have to download and install this tool on each computer manually. An example of usage PsGetSID to get a SID by a user account name:
PsGetSid PC1\jjsmith
To get username by SID use the command:
PsGetSid S-1-5-21-1175651296-1316133944-203321314-1005
In my opinion, the easiest way to convert SID -> Username and Username -> SID is to use the internal Windows CLI tools or simple PowerShell cmdlets:
How to Find a Local User SID?
To get the SID of the local user account on a current computer, you can use the wmic tool, which allows you to query the computer’s WMI namespace. To get the SID of the local user test_user, you can use the WMIC command:
wmic useraccount where name='test_user' get sid
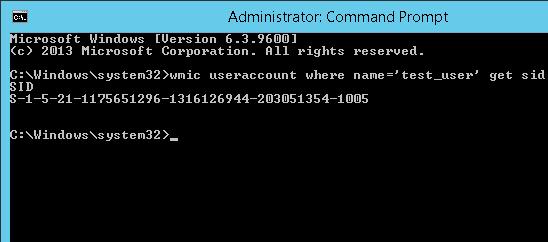
The command above returned the SID of the specified local user. In this example – S-1-5-21-1175659216-1321616944-201305354-1005.
If you need to get the SID of the current user (under which the command is executed), run the following command:
wmic useraccount where name='%username%' get sid
Using the two .NET classes System.Security.Principal.SecurityIdentifier and System.Security.Principal.NTAccount you can get the SID of the local user with PowerShell:
$objUser = New-Object System.Security.Principal.NTAccount("LOCAL_USER_NAME")
$strSID = $objUser.Translate([System.Security.Principal.SecurityIdentifier])
$strSID.Value
How to Get SID for an Active Directory User/Group?
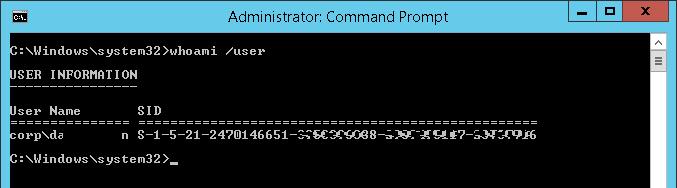
The following command can be used to get a SID of the current domain account:
whoami /user
You can find out the domain user SID using WMIC tool. You must specify your domain name in the following command:
wmic useraccount where (name='jjsmith' and domain=′corp.contoso.com′) get sid
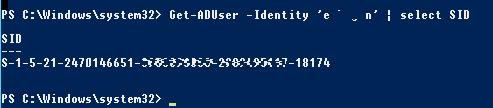
To find the SID of an AD domain user, you can use the Get-ADUser cmdlet that is part of the Active Directory Module for Windows PowerShell. Get the SID for the jjsmith account:
Get-ADUser -Identity 'jabrams' | select SID
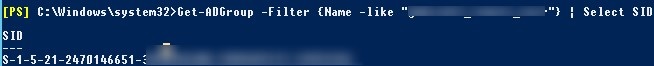
You can get the SID of an AD group using the Get-ADGroup cmdlet:
Get-ADGroup -Filter {Name -like "fr-sales-*"} | Select SID
If the PowerShell AD module is not installed on your computer, you can get the user’s SID from AD domain using the .Net classes mentioned earlier:
$objUser = New-Object System.Security.Principal.NTAccount("corp.contoso.com","jabrams")
$strSID = $objUser.Translate([System.Security.Principal.SecurityIdentifier])
$strSID.Value

The same PowerShell one-liner command:
(new-object security.principal.ntaccount “jabrams").translate([security.principal.securityidentifier])
How to Convert a SID to User/Group Name?
To get the name of the user account by the SID (a reverse procedure), you can use one of the following commands:
wmic useraccount where sid='S-1-3-12-12451234567-1234567890-1234567-1434' get name
You can get the user name by a SID using the AD module for PowerShell:
Get-ADUser -Identity S-1-3-12-12451234567-1234567890-1234567-1434
To find the domain group name by a known SID, use the command:
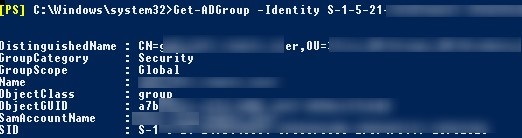
Get-ADGroup -Identity S-1-5-21-247647651-3965464288-2949987117-23145222
You can also find out the group or user name by SID with the built-in PowerShell classes (without additional modules):
$objSID = New-Object System.Security.Principal.SecurityIdentifier ("S S-1-3-12-12451234567-1234567890-1234567-1434")
$objUser = $objSID.Translate( [System.Security.Principal.NTAccount])
$objUser.Value
Searching Active Directory by SID
If you don’t know what type of AD object a certain SID belongs to and what exact PoSh cmdlet to use to find it (Get-AdUser, Get-ADComputer or Get-ADGroup), you can use the universal method of searching objects in Active Directory domain ba a SID using the Get-ADObject cmdlet.
$sid = ‘S-1-5-21-2412346651-123456789-123456789-12345678’
Get-ADObject –IncludeDeletedObjects -Filter "objectSid -eq '$sid'" | Select-Object name, objectClass
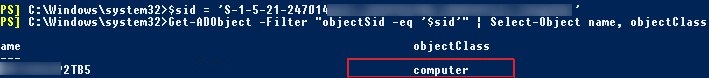
In our case, the AD object with the specified SID is a domain computer (see the objectClass attribute).