Historically, the WindowsUpdate.log plain text file has been used to analyze the operation of the Windows Update agent and service. However, the Windows Update logs in Windows 10 (Windows Server 2016/2019) are saved in the Event Tracing for Windows file format (ETW), instead of the usual text file. With such an action, the Windows developers planned to increase the performance of the logging subsystem and reduce the space occupied by the text files on the disk.
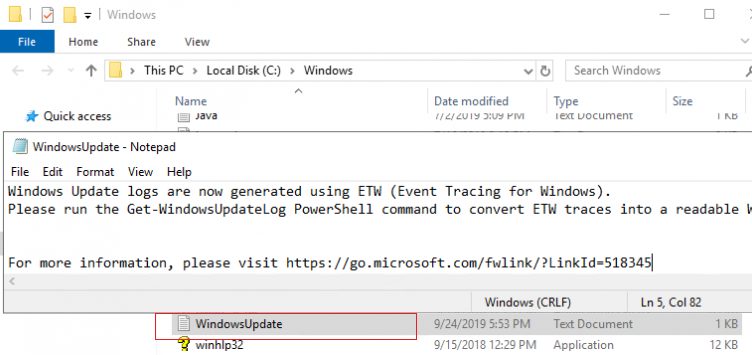
Thus, Windows Update events are no longer written in real time to the %windir%\WindowsUpdate.log file. Even though the file is still present in the root of the Windows folder, it only says that the ETW format is now used to collect WU logs.Windows Update logs are now generated using ETW (Event Tracing for Windows).
Please run the Get-WindowsUpdateLog PowerShell command to convert ETW traces into a readable WindowsUpdate.log.
For more information, please visit http://go.microsoft.com/fwlink/?LinkId=518345
The disadvantage of the new logging method for administrators – now you can’t quickly analyze the Windows Update Agent service, find error codes in the WindowsUpdate.log text file, check the WSUS agent settings and analyze the update installation history.
You can convert ETW events to the plain text WindowsUpdate.log file for more convenient analysis of update service events. To do this, use the PowerShell cmdlet – Get-WindowsUpdateLog. This cmdlet allows you to collect information from all .etl files (they are stored in C:\WINDOWS\Logs\WindowsUpdate) and create a single WindowsUpdate.log text file.
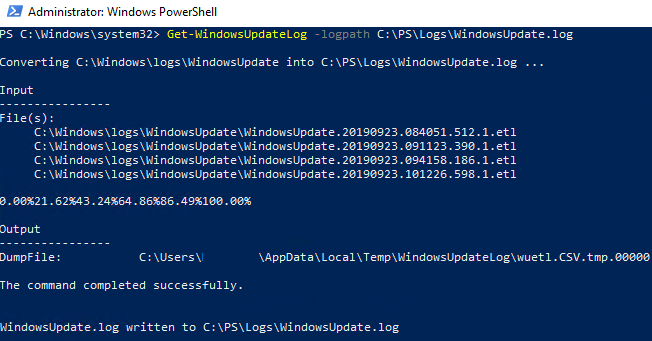
To generate the WindowsUpdate.log file and save it in the C:\PS\Logs, run the following command in the PowerShell console:
Get-WindowsUpdateLog -logpath C:\PS\Logs\WindowsUpdate.log
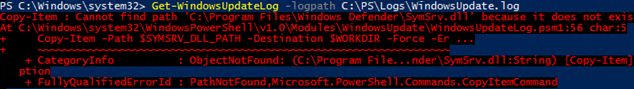
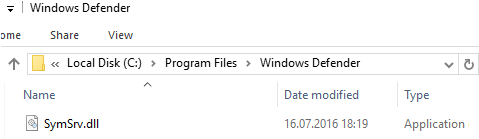
In Windows Server 2016, when you run the Get-WindowsUpdateLog cmdlet, you may receive the error “SymSrv.dll is missing”:
Copy-Item : Cannot find path 'C:\Program Files\Windows Defender\SymSrv.dll' because it does not exist. At C:\Windows\system32\WindowsPowerShell\v1.0\Modules\WindowsUpdate\WindowsUpdateLog.psm1:56 char:5
The file “C:\Program Files\Windows Defender\SymSrv.dll” is usually missing if the Windows Defender is not installed on the server.
To fix the error, you can install Windows Defender, copy the SymSrv.dll file from another Windows Server 2016/Windows 10, or search for the file SymSrv.dll in the local WinSxS folder (in my case, the directory was called C:\Windows\WinSxS\amd64_windows-defender-service-cloudclean_…) and copy it to the “C:\Program Files\Windows Defender” folder.
In older Windows 10 builds, the first time you run the Get-WindowsUpdateLog cmdlet, it downloads and installs the Microsoft Internet Symbol Store. Newest versions of Windows 10 access the Microsoft Character Server in Azure online. Then the cmdlet:
- Reads the data from all .etl files;
- The data is converted into CSV (by default) or XML format;
- The data from the file in an intermediate format will be converted and added to the log text file specified in the LogPath parameter (if the parameter in LogPath is not specified, WindowsUpdate.log is created on the desktop of the user running the command)
Open the log file using this PowerShell command:
Invoke-Item -Path C:\PS\Logs\WindowsUpdate.log
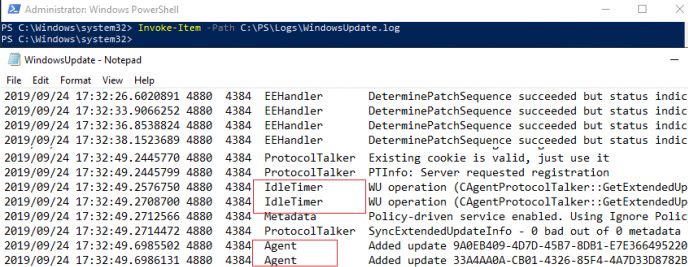
In some cases, in the WindowsUpdate.log file you can see such strings:
Unknown(140): GUID=53212e4cc-4321-f43a-2123-9ada0090bc12b (No Format Information found).
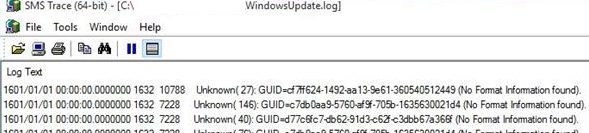
This means that you don’t have the Windows Symbol server installed (today you cannot download a separate Windows symbols installer, because it is automatically downloaded from the symbol store in Azure). For isolated environments, you can use the offline version of the symbol server according to the article Offline Symbols for Windows Update.
Please, note that the created WindowsUpdate.log file is static and is not updated in real time as in previous Windows versions. To update the file, you need to run Get-WindowsUpdateLog cmdlet once again or create a script that automatically updates the file at some frequency (the file is overwritten).
It is quite difficult to analyze the resulting WindowsUpdate.log file, because it collects data from many event sources:
- AGENT – Windows Update agent events;
- AU – automatic update;
- AUCLNT – user interaction;
- HANDLER – update installer management;
- MISC – common WU info;
- PT – synchronization of updates with local datastore;
- REPORT – reports collection;
- SERVICE – wuauserv service start/stop events;
- SETUP – installing new versions of the Windows Update client;
- DownloadManager – downloading updates to local cache using BITS;
- Handler, Setup – installer headers (CBS , etc.);
- and many others.
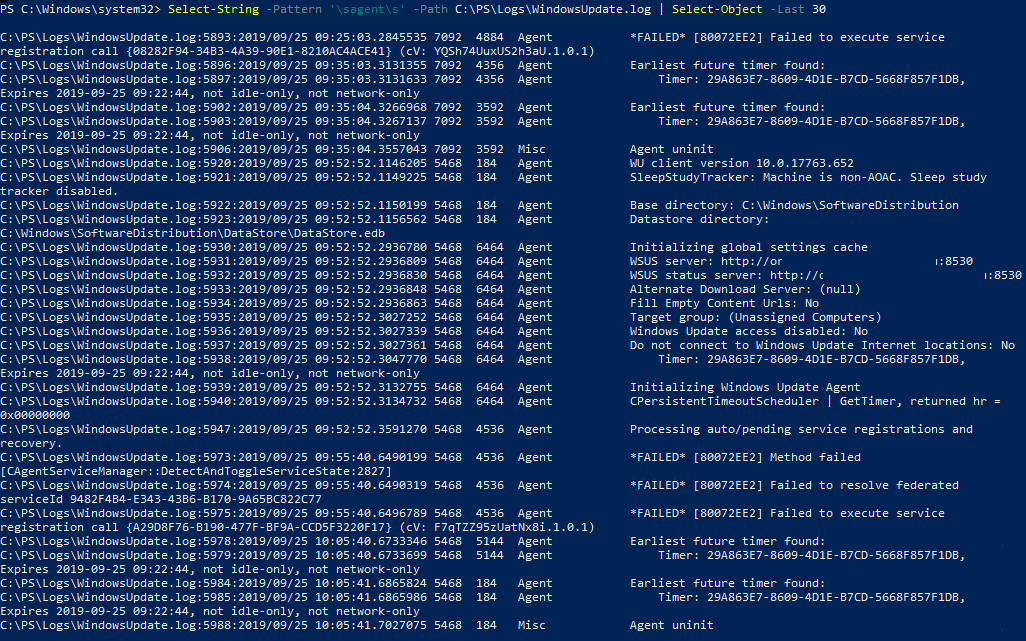
You can select the last 30 events from the Windows Update Agent (agent) with a simple regular expression:
Select-String -Pattern '\sagent\s' -Path C:\PS\Logs\WindowsUpdate.log | Select-Object -Last 30
You can filter events in the WindowsUpdate.log by several sources:
Select-String -Pattern '\sagent\s|\smisc\s' -Path c:\PS\Logs\WindowsUpdate.log | Select-Object -Last 50
Similarly, you can parse the text file for events by KB number, errors (FAILED, Exit Code, FATAL).
You can also generate the WindowsUpdate.log file for the remote computer or server:
Get-WindowsUpdateLog -ETLPath \\ny-srf-1\C$\windows\Logs\WindowsUpdate -LogPath C:\PS\Logs\windowsupdate-ny-srf-1.log
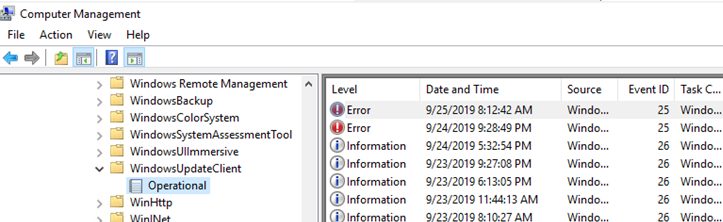
You can also use Event Viewer logs to analyze the operation of the Windows Update service. Expand the following Event View section: Applications and Services Logs -> Microsoft -> Windows –> WindowsUpdateClient -> Operational.