In this post we’ll consider how to find domain controllers with FSMO roles in Active Directory, how to transfer one or more FSMO roles to another (additional/secondary) domain controller and how to seize FSMO roles in case of a failure of the domain controller FSMO role owner.
Understanding FSMO Roles in Active Directory Domain
What are FSMO (Flexible Single Master Operation) roles in an Active Directory domain? You can perform most standard operations in Active Directory (like creating new user accounts and security groups or joining a computer to a domain) on any domain controller. The AD replication service is responsible for distributing these changes throughout the AD directory. Different conflicts (for example, simultaneous renaming of a user account on several domain controllers) are resolved using a simple principle — the last one is right. However, there is a number of operations during which a conflict is unacceptable (for example, when creating a new child domain/forest, changing the AD schema, etc.). To perform operations that require uniqueness, you need the domain controllers with the FSMO roles. The main task of the FSMO roles is to prevent such conflicts.
There may be five FSMO roles in an Active Directory domain.
Two roles are unique for an AD forest:
- The Schema master is responsible for making changes to the Active Directory schema (for example, when extending AD schema using the
adprep /forestprepcommand; - The Domain naming master provides unique names for all domains and application sections you create in your AD forest (to manage it you need “Enterprise admins” privileges).
And there are three roles for each domain (to manage them, your account must be a member of the “Domain Admins” group):
- The PDC emulator is the main browser in your Windows network (Domain Master Browser is used to show computers in the network environment), it tracks user lockouts when entering wrong passwords, it is the main NTP server in your domain, it is used to provide compatibility with clients running Windows 2000/NT, it is used by DFS root servers to update the namespace information;
- The Infrastructure Master is responsible for updating the cross-domain object links; and the
adprep /domainprepcommand is run on it; - The RID Master — the server distributes RIDs (in packs by 500 pieces) to other domain controllers to create unique object identifiers (SIDs).
How to List FSMO Role Owners in a Domain?
How can you find out which domain controllers are FSMO role holders in your Active Directory domain?
In order to find all FSMO role owners in domain, run the command:
netdom query fsmo
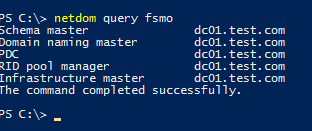
Schema master dc01.test.com Domain naming master dc01.test.com PDC dc01.test.com RID pool manager dc01.test.com Infrastructure master dc01.test.com
You can view FSMO roles for another domain:
netdom query fsmo /domain:contoso.com
In this example you can see that all FSMO roles are located on the DC01. When deploying a new AD forest (domain) , all FSMO roles are placed to the first DC. Any domain controller, except RODC, may be a holder of any FSMO role. Accordingly, the domain administrator can transfer any FSMO role to any other domain controller.
You can get the information about FSMO roles in your domain via PowerShell using the Get-ADDomainController cmdlet (the RSAT Active Directory for PowerShell module must be installed):
Get-ADDomainController -Filter * | Select-Object Name, Domain, Forest, OperationMasterRoles |Where-Object {$_.OperationMasterRoles}
Or you can view the forest or domain level FSMO roles as follows:
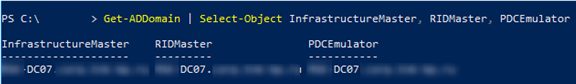
Get-ADDomain | Select-Object InfrastructureMaster, RIDMaster, PDCEmulator
Get-ADForest | Select-Object DomainNamingMaster, SchemaMaster
Here are the general Microsoft recommendations for FSMO role placement in the domain:
- Place forest level roles (Schema master and Domain naming master) on the root domain that is the Global Catalog server at the same time;
- Place all three domain FSMO roles on one domain controller with the suitable performance;
- All forest DCs must be Global Catalog servers since it improves AD reliability and performance. Then the Infrastructure Master role is actually not necessary. If you have a DC without the Global Catalog role, place Infrastructure Master role on it.
- Don’t place any other tasks on the FSMO roles owner DCs.
You can transfer FSMO roles in Active Directory using several methods: using AD MMC graphic snap-ins, ntdsutil.exe or PowerShell. Transferring FSMO roles is relevant when optimizing your AD infrastructure, or a DC that holds FSMO role has suffered catastrophic hardware/software failure. There are two ways of moving FSMO roles: transferring (when both DCs are available) or seizing (when a DC with a FSMO role is not available or has been broken).
How to Transfer FSMO Roles with PowerShell?
The easiest and fastest way to transfer FSMO roles in a domain is using the Move-ADDirectoryServerOperationMasterRole PowerShell cmdlet.
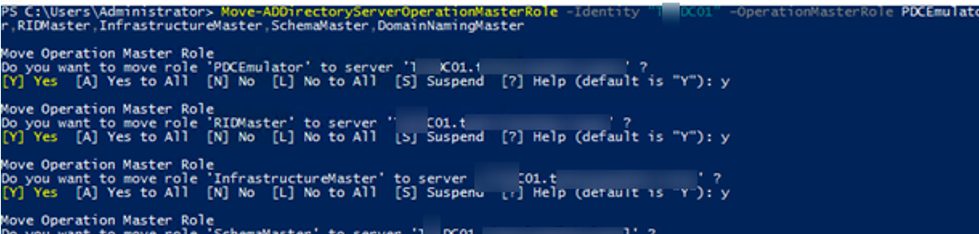
You can transfer one or more FSMO roles at a time to the specified DC. The following command will move two roles to DC02:
Move-ADDirectoryServerOperationMasterRole -Identity dc03 -OperationMasterRole PDCEmulator, RIDMaster
In the OperationMasterRole argument, you can specify either the name of the FSMO role or its index according to the following table:
| PDCEmulator | 0 |
| RIDMaster | 1 |
| InfrastructureMaster | 2 |
| SchemaMaster | 3 |
| DomainNamingMaster | 4 |
The previous command in a shorter form looks like this:
Move-ADDirectoryServerOperationMasterRole -Identity dc02 -OperationMasterRole 0,1
To transfer all FSMO roles at once to the additional domain controller, run this command:
Move-ADDirectoryServerOperationMasterRole -Identity dc03 -OperationMasterRole 0,1,2,3,4
Transferring FSMO Roles using Active Directory Graphic Snap-ins
To move FSMO roles, you can use standard Active Directory graphic snap-ins. The transfer operation is preferably performed on a DC with the FSMO role. If the server local console is not available, use the Change Domain Controller option and select the domain controller in the MMC snap-in.
How to Transfer RID Master, PDC Emulator & Infrastructure Master Roles?
To transfer domain-level roles (RID, PDC, Infrastructure Master), the Active Directory Users and Computers (DSA.msc) console is used.
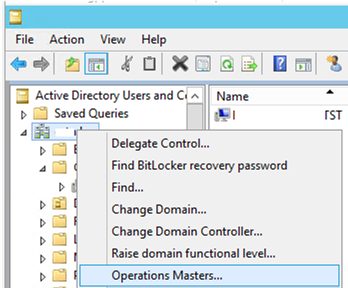
- Open the Active Directory Users and Computers (ADUC) snap-in;
- Right-click your domain name and select Operations Master;

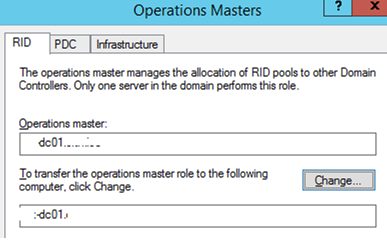
- A window with three tabs (RID, PDC, Infrastructure) appears. Use these tabs to transfer the corresponding roles by specifying new FSMO owner and clicking the Change button.

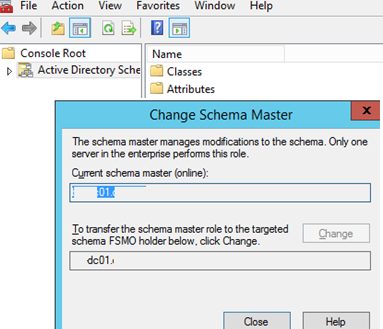
How to Transfer Schema Master Role?
To transfer the forest-level Schema Master FSMO, the Active Directory Schema snap-in is used.
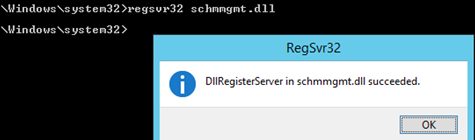
- Prior to starting the snap-in, you must register the schmmgmt.dll library by running
regsvr32 schmmgmt.dllin the command prompt;
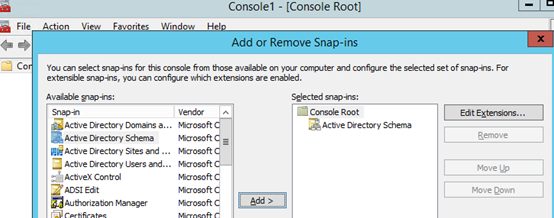
- Open the MMC console, by typing MMC in the command prompt;
- Select File -> Add/Remove snap-in from the menu and add the Active Directory Schema console;

- Right-click the console root (Active Directory Schema) and select Operations Master;
- Enter the domain controller name you want to transfer the Schema Master role to, then click Change and OK. If the button is not available, make sure that your account is a member of the Schema admins group.

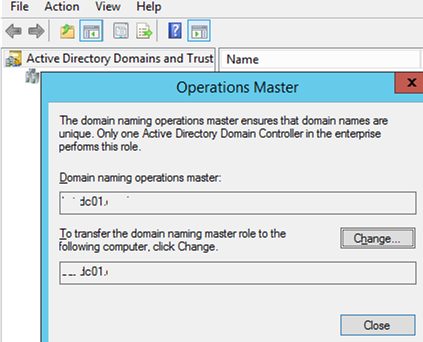
How to Transfer Domain Naming Master FSMO?
- To transfer the Domain Naming Master FSMO role, open the Active Directory Domains and Trusts console;
- Right-click the name of your domain and select Operations Master;
- Click Change, enter the name of the domain controller and click OK.

Using Ntdsutil.exe to Transfer FSMO Roles from the Command Prompt
Important. Use the ntdsutil.exe tool carefully and make sure you know what you are doing or you can break your Active Directory domain!
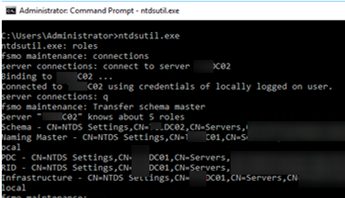
- Run the command prompt on your domain controller and run:
ntdsutil - Enter this command:
roles - Then:
connections - Then you must connect to the DC you want to transfer FSMO roles to. To do it, enter:
connect to server <servername> - Type
qand press Enter; - To transfer an FSMO role, use this command:
transfer <role>, where <role> is the role you want to transfer. For example:transfer schema master,transfer RID, etc;
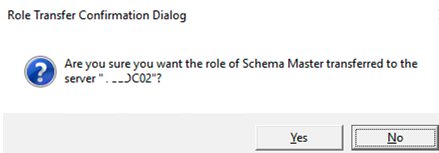
- Confirm the FSMO role transfer;

- When it is done, press
qand then Enter to quit ntdsutil.exe; - Restart the domain controller.
Seizing AD FSMO Roles
If a DC with one of FSMO roles has been broken (and cannot be recovered) or is unavailable for a long time, you can force seize any of its roles. However, it is very important to make sure that the server you seize the role from must never appear in the network if you do not want any new problems with AD (even if you later restore the DC from the backup ). If you want to return the broken DC to the domain, the only correct method is to remove it coputer account from AD, perform a clean Windows install with a new hostname, install the ADDS role and promote the server to the domain controller.
You can seize FSMO roles using PowerShell or NTDSUtil.
The easiest way to seize an FSMO role is through PowerShell. To do it, the same Move-ADDirectoryServerOperationMasterRole cmdlet is used, but the –Force parameter is added to it.
For example, to seize the PDCEmulator role and force transfer it to DC02, run the command:
Move-ADDirectoryServerOperationMasterRole -Identity DC2 -OperationMasterRole PDCEmulator –Force
You can also seize FSMO roles to your DC02 server using ntdsutil.exe. The role seizure is similar to the common transfer. Use the following commands:
ntdsutil
roles
connectionsconnect to server DC02 (the server you transfer a role to)quit
To seize different FSMO roles, use these commands:
seize schema master
seize naming master
seize rid master
seize pdc
seize infrastructure master
quit