In this post we will show how to use the built-in Windows 10 OpenSSH server to forward ports via an SSH tunnel. SSH port forwarding allows you to tunnel (forward) app ports from a local computer to a remote server and vice versa. Earlier SSH tunneling was used in Linux/Unix environment only, but today you can use it in Windows 10/Windows Server 2016 as well. Here is a case study of how to use an RDP connection through the SSH tunnel (TCP port 22) on Windows.
SSH tunneling is mostly used in the scenarios when you need to connect to a remote computer behind the firewall. For example, you have a Windows Server with only SSH port open (TCP 22). All other ports are blocked by a hardware firewall or Windows Firewall. Your task is to connect to the Windows Server using the RDP client. It seems impossible since Remote Desktop port 3389 is blocked by the firewall. However, you can use the port forwarding technique through the SSH tunnel.
Here are the typical usage scenarios of SSH tunneling:
- Local TCP forwarding is a local port forwarding to a remote server;
- Remote TCP forwarding is a remote port forwarding to a local computer;
- Double SSH tunnel connects computers without any dedicated pubic IP addresses behind NAT through an SSH server.
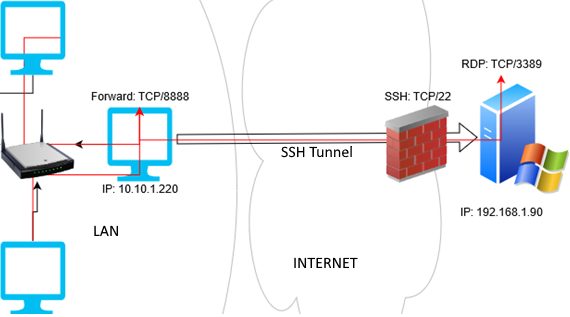
RDP Access Through SSH Tunnel (Local TCP Forwarding)
In this mode, you create a local TCP port on your computer. All connections to this port are forwarded to the specified port on a remote server via the SSH tunnel. In this example, we will create a local Port 8888, and the connection to it will be forwarded to the RDP port 3389 on a remote Windows computer. The general connection scheme is shown below.
To create an SSH tunnel using the built-in Windows 10 SSH client (is a part of Windows starting from Windows 10 1809 and Windows Server 2019), run this command:
ssh -L 8888:192.168.1.90:3389 [email protected] To make the SSH tunnel work in the background, add the –f parameter.
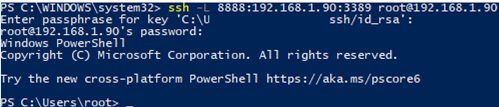
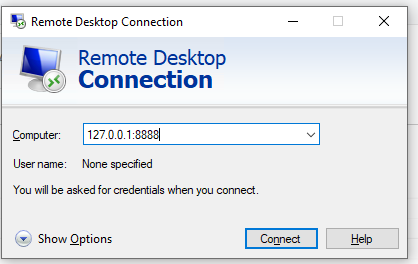
To connect to a remote computer desktop via the SSH tunnel, you need to connect to the local Port 8888 of your computer using the RDP client (mstsc.exe):
127.0.0.1:8888
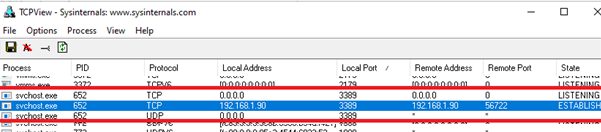
Login to the remote computer and work safely in the RDP session ( but you remember that port 3389 is still closed by the firewall). You can use the TCPView tool to make sure that the RDP connection is local (the RDP connection is initiated by the SSH server running locally).
Please note that if you forward an unencrypted app traffic, it will be transmitted encrypted over the public networks. Such a traffic will be encrypted on the one end of your SSH connection and decrypted on the other one.
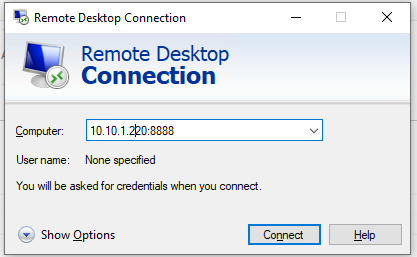
Other computers of your local network can also use this mode to connect to an RDP server even if the direct connection is not allowed (both via SSH and via RDP). To do it, they must connect via RDP client to port number 8888 on your computer with the SSH tunnel created:
mstsc.exe /v 10.10.1.220:8888
Remote TCP Forwarding to a Local Computer
There is another SSH tunnel use case — remote TCP forwarding. Using the SSH tunnel, you can allow the remote server to access a local port on your computer or a port on another computer in your local network. For example, you want an external server (200.168.1.90) access your Intranet site (not published in the Internet). To create a reverse SSH tunnel, use this command:
ssh -R 8080:internalwww:80 [email protected]
To get access to internalwwww site from a remote SSH server, it is enough to type this address in the browser: http://localhost:8080In all Windows versions you can create port forwarding rules using the netsh interface portproxy command
Using SSH tunnels, you can build port forwarding chains. To enable or disable SSH tunneling, add one of the following directives in the OpenSSH config file (%programdata%\ssh\sshd_config):
AllowStreamLocalForwarding yes AllowTcpForwarding remote