To perform some actions in Windows, it’s not enough to have administrator privileges. For example, you cannot replace or delete system files and some registry keys, stop system services or perform some other potentially unsafe actions that could affect the stability of your operating system. In these cases, a system administrator can take ownership of files or other objects, or perform actions on behalf of the system account. In this post we’ll look at how to run an app or the command prompt as the privileged SYSTEM (LocalSystem) account on Windows 10.
Making changes to a Windows image on behalf of the SYSTEM account is a non-standard operation. Please note that incorrect actions taken with the NT AUTHORITY\SYSTEM privileges may break your OS. In practice, running processes as System account is rarely used. In most cases you can solve a problem using some standard ways: runas, run an app without administrator privileges and suppressing the UAC prompt, take ownership on files/registry keys, disable UAC for all or only certain apps, grant service management privileges for non-admin users.
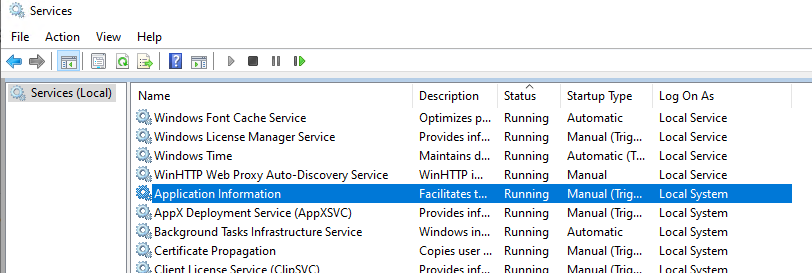
The built-in SYSTEM account is used by the SCM (Service Control Manager) to run and manage system services. Using the System account (it may be also called NT AUTHORITY\SYSTEM, Local System or Computer\LocalSystem), most system services and processes are run (including NT OS Kernel). Open the service management mmc snap-in (services.msc) and note the services that have Local System in the LogOnAs column. These services are running under the SYSTEM account.
How to Run CMD under Local System Account in Windows (Versions Prior to Vista)?
In Windows XP and Windows Server 2003 (no longer supported), there was an interesting trick that allowed you to run a program or the interactive command prompt (cmd.exe) with the system privileges using the Task Scheduler. It was enough to open the command prompt under the admin account and run the following command:
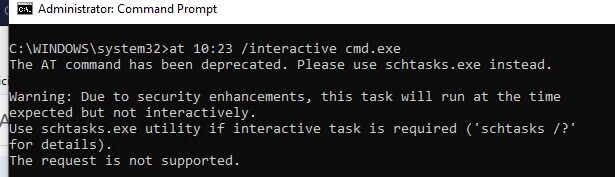
at 10:23 /interactive cmd.exe
where, 10:23 is the current time + one minute (in the 24-hour format)
When the specified time comes, a command prompt will appear running under the local system account. If you have run this command in a terminal (RDP) session on Windows Server 2003/XP, note that the command prompt with the System privileges is displayed in the console session only (you can connect to the computer console via mstsc /console or mstsc /admin).
Windows 10 doesn’t support running the interactive command prompt using the at command. It is recommended to use schtasks.exe instead.
Warning: Due to security enhancements, this task will run at the time expected but not interactively.
Use schtasks.exe utility if interactive task is required ('schtasks /?' for details).
The request is not supported.
How to Run CMD/Process as SYSTEM on Windows 10 Using PSExec?
In Windows 7 or higher, the interactive command prompt cannot be run under the System account using Task Scheduler. To run commands as NT Authority\ System, you can use the PSExec.exe utility by Sysinternals. You can download the PSExec.exe tool from Microsoft’s website: https://docs.microsoft.com/en-us/sysinternals/downloads/psexec. In most cases, it is used to manage Windows remotely, and it also has a useful feature for running processes on behalf System account. Some antiviruses may identify PSExec.exe as a potentially harmful program (by the way, it was psexec that was used to distribute the notorious notpetya virus).
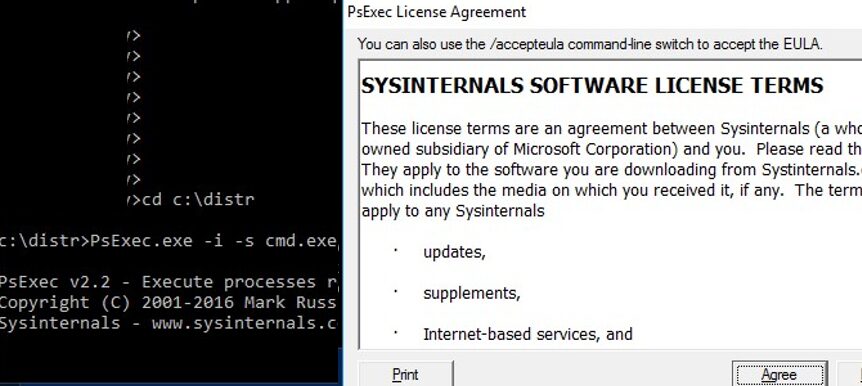
PSExec doesn’t need to be installed. Open the elevated command prompt (“Run as administrator”), go to the folder where PSexec.exe is located and run the following command:
psexec -i -s cmd.exe
-i – allows to start the process/app in the interactive mode (a user can interact with the app on the desktop; if you don’t use this parameter, the process starts in a console session),
–s – means that the process (in this case, the command prompt) must be run as System account. On first PsExec run, you will be prompted to accept a license agreement.
After running the command, a new command prompt window will appear run under the NT Authority\System account. Make sure it is true, by running this command:
whoami
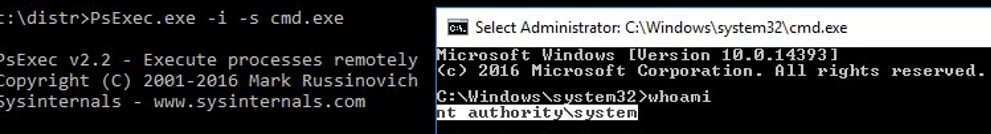
Thus, you can run any program, command or script as System account. It is enough to replace cmd.exe in the PsExec parameter with the name of the app executable you want to run.
In the command prompt window that appears, you can run any commands as SYSTEM. Now you can change, rename or delete system files/registry keys that are owned by TrustedInstaller or SYSTEM. All programs or processes you start in this window will run with elevated LocalSystem privileges. For example, you can stop a system service or close a file opened by the system process. Using PSExec, you can open the interactive command prompt with the NT AUTORITY\SYSTEM privileges on a remote computer. To do it, the following command is used:
psexec -s \\my-test-pc cmd.exe
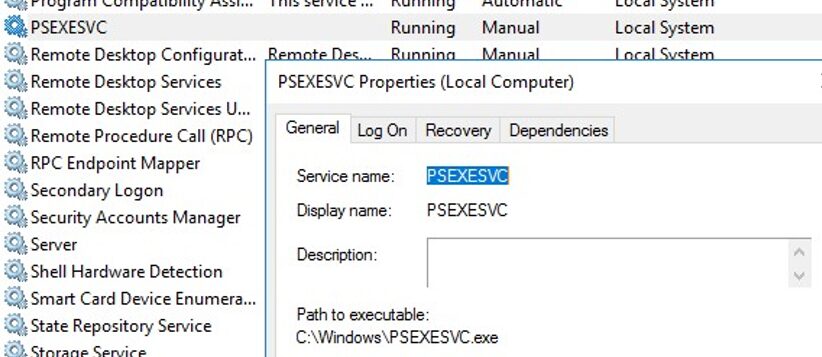
If the “Couldn’t install PSEXESVC service” error appears, make sure that:
- The command prompt is run as administrator;
- Another PSEXESVC service instance is not running

There is also a number of third-party tools to run apps as System account (AdvancedRun , RunAsSystem, PowerRun), but I cannot see any point in using them. First of all, they are third-party and you cannot be sure there is no malicious code in them. Secondly, the official PsExec utility by Microsoft does a great job.