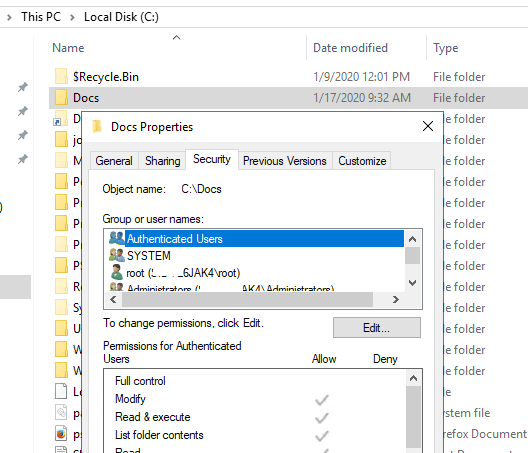
In order to manage access to files or folders in Windows, a special ACL (Access Control List) is assigned to an NTFS file system object (a file or a folder). The ACL of the object defines available operations (permissions) that a user or groups can perform with file system object. In most cases, Windows administrators use the File Explorer graphic interface (file/folder properties -> Security tab) or icacls console tool to manage NTFS permissions on files or folders. In this post we will look on how to manage permissions on the NTFS objects using the PowerShell cmdlets. You can use these commands in your scripts or to automate the management of NTFS access permissions on Windows file servers and workstations.
Get-Acl & Set-Acl: the Built-in PowerShell Cmdlets to Manage NTFS ACLs
In PowerShell v5 (Windows 10/Windows Server 2016), there are two separate built-in cmdlets to manage ACL (a part of the Microsoft.PowerShell.Security module):
- Get-Acl — allows to get current ACLs for the specific object on the NTFS file system;
- Set-Acl – is used to add/change current object ACL.
We won’t look at these built-in cmdlets in detail, since their features in most cases are not enough to manage NTFS permissions in real tasks. Let’s dwell on some typical use cases.
To get the current owner of a folder (file) and the list of assigned NTFS permissions, run the command:
get-acl C:\docs\ |fl
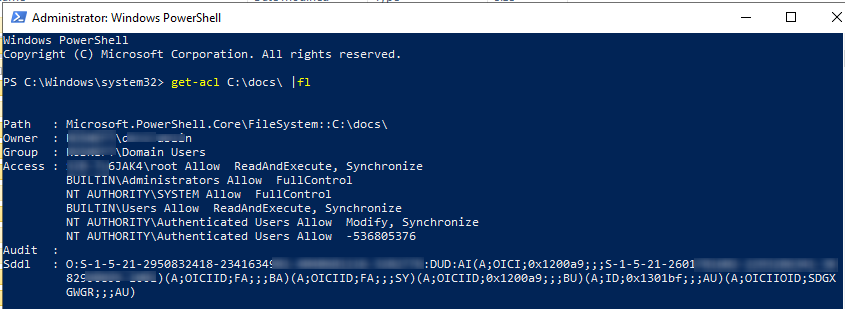
Path : Microsoft.PowerShell.Core\FileSystem::C:\docs\ Owner : CORP\asmith Group : CORP\Domain Users Access : PC-7L7JAK6\root Allow ReadAndExecute, Synchronize BUILTIN\Administrators Allow FullControl NT AUTHORITY\SYSTEM Allow FullControl BUILTIN\Users Allow ReadAndExecute, Synchronize NT AUTHORITY\Authenticated Users Allow Modify, Synchronize NT AUTHORITY\Authenticated Users Allow -536805376 Audit : Sddl : O:S-1-5-21-2950832418-2342342341-4040681116-234234G:DUD:AI(A;OICI;0x1200a9;;;S-1-5-21-2601781602-2342342341-6543210895-1001)(A;OICIID;FA;;;BA)(A;OICIID;FA;;;SY)(A;OICIID;0x1200a9;;;BU)(A;ID;0x1301bf;;;AU)(A;OICIIOID;SDGXGWGR;;;AU)
As you can see, the current permissions are also displayed as the SDDl string.
You can display the lists of NTFS permissions only in a clearer format:
(get-acl C:\docs\).access
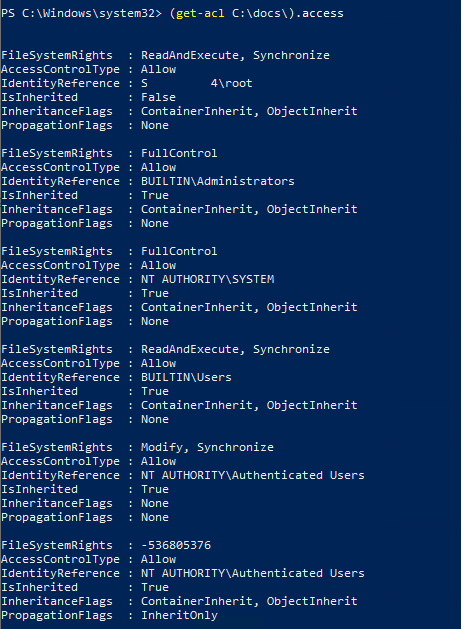
You can copy the current NTFS permissions from one NTFS folder (object) and apply them to another one:
Get-Acl e:\old_docs | Set-Acl C:\docsTo do it, the account must be the owner of the object and have Take Ownership privilege.
The main problem of using Set-ACL is that the cmdlet is always trying to change the resource owner, even if you just need to change the NTFS permissions. So to add the permissions on an object, you have to use the following complex script:
$path = "c:\docs "
$user = "contoso\john.smith"
$Permiss = "Read, ReadAndExecute, ListDirectory"
$InheritSettings = "Containerinherit, ObjectInherit"
$PropogationSettings = "None"
$RuleType = "Allow"
$acl = Get-Acl $path
$perm = $user, $Permiss, $InheritSettings, $PropogationSettings, $RuleType
$rule = New-Object -TypeName System.Security.AccessControl.FileSystemAccessRule -ArgumentList $perm
$acl.SetAccessRule($rule)
$acl | Set-Acl -Path $path
To remove the NTFS permission to access a folder for a user or a group:$path = "c:\docs"
$acl = Get-Acl $path
$rules = $acl.Access | where IsInherited -eq $false
$targetrule = $rules | where IdentityReference -eq "contoso\john.smith"
$acl.RemoveAccessRule($targetrule)
$acl | Set-Acl -Path $path
To disable folder inheritance from PowerShell:
$path = 'C:\docsAlso, using the Get-Acl and Set-Acl you can manage NTFS audit settings for the objects.
$acl = Get-ACL -Path $path
$acl.SetAccessRuleProtection($True, $True) # the first $True shows if the folder is protected, the second $True specifies if the current NTFS permissions have to be copied
Set-Acl -Path $path -AclObject $acl
Managing File Permissions with the NTFSSecurity PowerShell Module
As I have already mentioned, the built-in PowerShell cmdlets to manage file system object is not very convenient. To manage NTFS permissions on files and folders in Windows you should better use a separate module from the PowerShell gallery – NTFSSecurity. You can install the latest version of NTFSSecurity module (4.2.6, currently) using the Install-Module -Name NTFSSecurity command or download it manually here. When installing it manually, you just need to extract the module archive to the C:\Windows\System32\WindowsPowerShell\v1.0\Modules\NTFSSecurity.
Import the NTFSSecurity module to your PowerShell session:
Import-Module NTFSSecurity
Display the list of commands available in the module (36 cmdlets):
Get-Command -Module NTFSSecurity
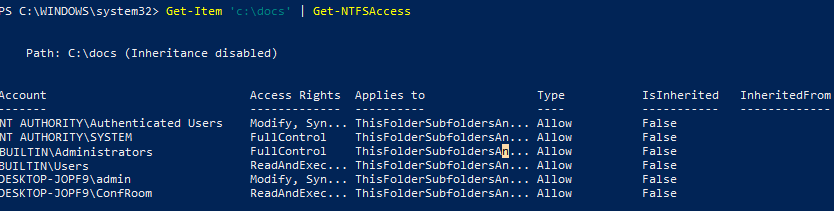
List the current NTFS permissions of the folder:Get-Item 'c:\docs' | Get-NTFSAccess
As you can see, the current permissions are shown in a more convenient form.
To grant a user or a group full control permission on a specific folder, run this command:Add-NTFSAccess -Path C:\docs -Account 'CORP\RShelby','BUILTIN\Administrators' -AccessRights 'Fullcontrol' -PassThru
Tip. By default, the NTFSSecurity cmdlets do not return any data. Use the -PassThru parameter to make the command display new ACLs after it is executed.
To grant permissions only at the top folder level and not to change permissions on the nested objects (folder only), use this command:
Add-NTFSAccess c:\docs\public -Account contoso\jane.doe -AccessRights Modify -AppliesTo ThisFolderOnly
To remove the assigned NTFS permissions:
Remove-NTFSAccess -Path C:\DOCS -Account 'contoso\jane.doe' -AccessRights FullControl -PassThru
The next command will remove the permissions for all nested objects in the folder for the given account (inherited permissions will be skipped):
Get-ChildItem -Path C:\docs -Recurse | Get-NTFSAccess -Account 'contoso\jane.doe' -ExcludeInherited |Remove-NTFSAccess -PassThru
With the following command, you can make the Administrator account an owner of all nested objects in the folder:
Get-ChildItem -Path C:\docs -Recurse -Force | Set-NTFSOwner -Account 'Administrator'
To clear all permissions assigned to folder objects manually (inherited permissions will not be removed):
Get-ChildItem -Path C:\docs -Recurse -Force | Clear-NTFSAccess
To enable NTFS inheritance for all objects in a folder:
Get-ChildItem -Path C:\docs -Recurse -Force | Enable-NTFSAccessInheritance
To display all permissions assigned manually except the inherited ones:
dir C:\docs | Get-NTFSAccess –ExcludeInherited
You can display the permissions assigned to the specific account (don’t confuse it with the effective permissions, we’ll discuss them later):
dir C:\docs | Get-NTFSAccess -Account contoso\john.smith
How to View NTFS Effective Permissions with PowerShell?
You can view the effective NTFS permissions for a specific file or a folder using the Get-EffectiveAccess cmdlet. Suppose, you have granted access to certain folder to several AD security groups and you want to know if the specific user account (or SID) can access the files folder. How can you do it without listing all the members of the AD groups that the user account belong to? This is the case when viewing effective NTFS permissions is very useful. For example, you need to view the effective permissions on all nested directories in a folder for the domain account jane.doe.
Get-ChildItem -Path c:\docs -Recurse -Directory | Get-NTFSEffectiveAccess -Account 'contoso\jane.doe’ | select Account, AccessControlType, AccessRights, FullName
Or you can view the effective permissions for a certain file:
Get-Item -Path 'C:\docs\annual_report2019.xlsx' | Get-NTFSEffectiveAccess -Account 'contoso\jane.doe' | Format-List
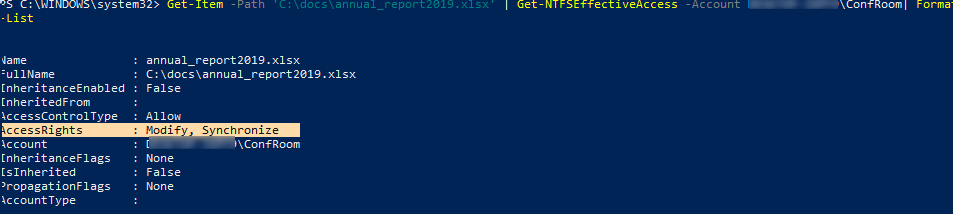
The current effective user permissions on the file system object are specified in the AccessRights field.