In this post I’ll talk about Active Directory domain controller backup and we’ll learn how to configure automatic AD backup using PowerShell and built-in Windows Server tools.
Do I Need to Back Up Active Directory?
Many times I have heard from my fellow administrators that if you have multiple (3, 8, etc.) domain controllers that are distributed across different geographic location, you don’t need to back up your AD at all. Since with multiple DCs you have provided domain fault tolerance. It is the schema when the simultaneous failure of all DCs tends to 0, and if one of the domain controllers fails, you can quickly deploy a new one on the same site and remove the old one using ntdsutil.
However, in my practice I have come across various scenarios when all domain controllers turned out to be damaged: in one case all domain controllers (although there were more than 20 of them in different cities) were encrypted due to a domain admin password capture by a ransomware using the mimikatz tool, in another case a replication of a damaged NTDS.DIT file resulted in a domain failure.
So you can and should back up your AD. You must backup at least key domain controllers and FSMO (Flexible single-master operations) role owners regularly. You can get the list of domain controllers with FSMO roles using this command:
netdom query fsmo
Get Last Active Directory Domain Controller Backup Date
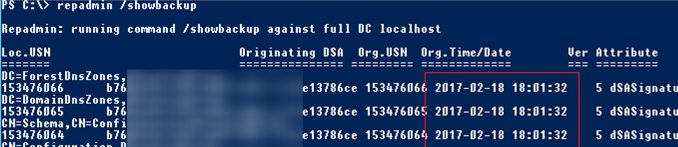
You can check when the current Active Directory domain controller was backed up last time using the repadmin tool:
repadmin /showbackup
You can see that in this example the last time the DC and AD partitions had been backed up was 2017-02-18 (it is likely, the backup has not been done since the domain controller was deployed).
You can get the backup status for all DCs in the domain using this command:
repadmin /showbackup *If your domain controllers are running on virtual machines and you back them up using snapshots, the backup dates won’t be updated. Most modern backup tools have an option you can check to specify that it is a DC and data in LDAP directory must be updated during backup.
Backing Up AD Domain Controller Using Windows Server Backup
If you don’t have any special backup software, you can use the built-in Windows Server Backup (this component has replaced the NTBackup tool). You can configure an automatic backup task in the Windows Server Backup GUI, but it has some restrictions. The main disadvantage is that a new server backup will always overwrite a previous one.
When you back up a domain controller using WSB, you create a System State backup. The System State includes the Active Directory database (NTDS.DIT), Group Policy Objects, SYSVOL directory contents, the registry, the IIS metadata, the AD CS database and other system files and resources. The backup is created through the Volume Shadow Copy Service (VSS).
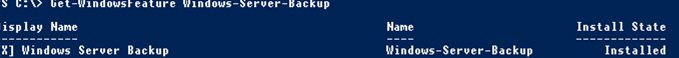
You can check if Windows Server Backup is installed using the Get-WindowsFeature PowerShell cmdlet:
Get-WindowsFeature Windows-Server-Backup
If WSB is not installed, you can add it with PowerShell:
Add-Windowsfeature Windows-Server-Backup –Includeallsubfeature
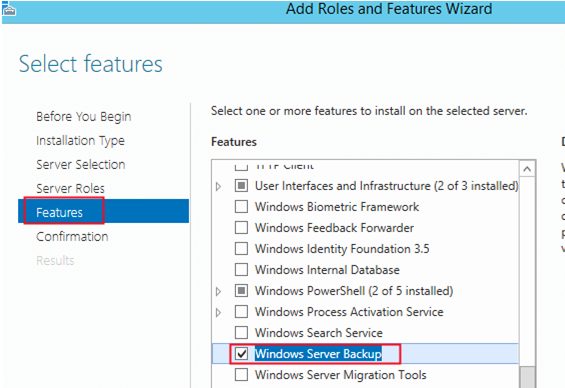
Or install Windows Server Backup via Server Manager -> Features.
I will save the backup of this AD domain controller to a shared network folder on a dedicated backup server. For example, a path to the backup directory may look like this: \\contoso-backup\backup\dc01. Configure the NTFS permissions for this folder: grant Read and Write access permissions to Domain Admins and Domain Controllers groups only.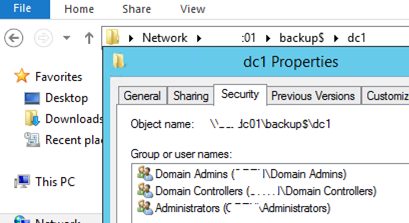
Active Directory Backup with PowerShell
Let’s try to back up a domain controller using PowerShell. To keep multiple levels of AD backup copies, we will store each backup copy in a separate directory with the date of backup creation as the folder name.
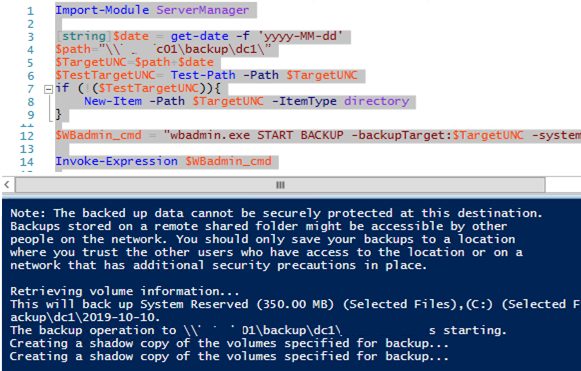
Import-Module ServerManager
[string]$date = get-date -f 'yyyy-MM-dd'
$path=”\\contoso-backup\backup\dc1\”
$TargetUNC=$path+$date
$TestTargetUNC= Test-Path -Path $TargetUNC
if (!($TestTargetUNC)){
New-Item -Path $TargetUNC -ItemType directory
}
$WBadmin_cmd = "wbadmin.exe START BACKUP -backupTarget:$TargetUNC -systemState -noverify -vssCopy -quiet"
Invoke-Expression $WBadmin_cmd
Run the PowerShell script. The wbadmin console will appear. It contains information about the process of disk backup (shadow copy) creation:
The backup operation to \\contoso-backup\backup\dc1\2020-06-01 is starting. Creating a shadow copy of the volumes specified for backup...
My first attempt to back up a DC failed up with an error (the domain controller was a VMWare virtual machine):
Detailed error: The filename, directory name, or volume label syntax is incorrect. The backup of the system state failed [01.06.2020 8:31].
I opened the WSB error log — C:\Windows\Logs\WindowsServerBackup\Backup_Error-01-06-2020_09-23-14.log.
There was the following error in the file:
Error in backup of C:\windows\\systemroot\ during enumerate: Error [0x8007007b] The filename, directory name, or volume label syntax is incorrect.
Looking ahead, I will tell that the problem was in the incorrect path of a VMWware Tools driver.
To fix the error, start the elevate command prompt and run this command:
DiskShadow /L writers.txt
list writers detailed
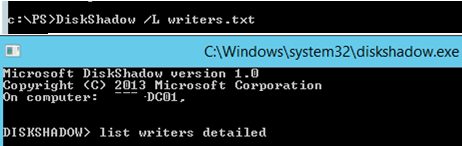
After getting the list, type quit and open C:\Windows\System32\writers.txt. Find the string containing “windows\\” in it.
In my case the string I had found looked like this:
File List: Path = c:\windows\\systemroot\system32\drivers, Filespec = vsock.sys
As you can see, a wrong path to the VSOCK.SYS driver is used.
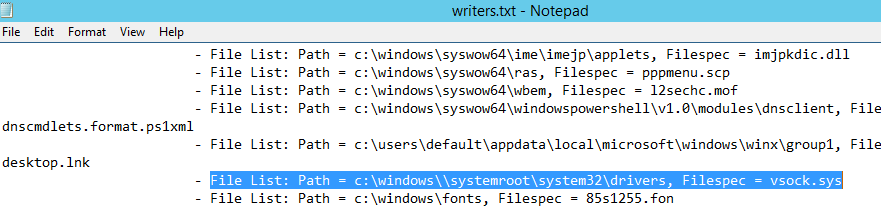
To correct the path, open the Registry Editor and go to reg key HKLM\SYSTEM\CurrentControlSet\Services\vsock.
Change the ImagePath value from\systemroot\system32\DRIVERS\vsock.sys
toSystem32\DRIVERS\vsock.sys
Run the backup script again.
If the backup has been successful, you will see the following messages in the log:
The backup operation successfully completed. The backup of volume (C:) completed successfully. The backup of the system state successfully completed [01.06.2020 09:52].
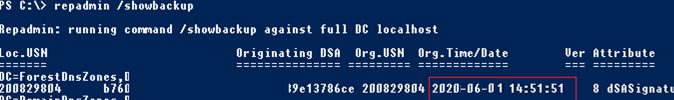
Check the time of the last DC backup:
repadmin /showbackup
Now it says that the last domain controller backup was performed today.
The size of the directory with the domain controller backup on the server is about 9GB. In fact, we have got a VHDX file you can use to restore the OS from WSB, or you can manually mount the VHDX file and copy the files or folders you need from it.
If there are multiple DCs in Active Directory, you do not need to back up all of them. To save the space, it is enough to periodically backup the Active Directory database — ntds.dit file. To do it, use these commands:
$WBadmin_cmd = "wbadmin start backup -backuptarget:$path -include:C:\Windows\NTDS\ntds.dit -quiet"
Invoke-Expression $WBadmin_cmd
The size of such a backup will be only 50-500MB depending on the AD database size.
For automatic AD backup, create the C:\Temp\PS\Backup_AD_DC.ps1 script on your DC. Run it according to the schedule using Task Scheduler. You can create a Scheduler task from the GUI or with PowerShell. The main requirement is that the task must be run under the NT AUTHORITY\SYSTEM account with the Run with highest privileges option checked. For a daily AD domain controller backup, create the following task:
$Trigger= New-ScheduledTaskTrigger -At 02:00am -Daily
$User= "NT AUTHORITY\SYSTEM"
$Action= New-ScheduledTaskAction -Execute "PowerShell.exe" -Argument "C:\Temp\PS\Backup_AD_DC.ps1"
Register-ScheduledTask -TaskName "BackupAD-DC-daily" -Trigger $Trigger -User $User -Action $Action -RunLevel Highest –Force
So, we have configured an AD backup, and we will talk ways to restore AD from a domain controller system state backup in our next article.